#linux find process using port
Explore tagged Tumblr posts
Text
youtube
This has been around for a few months, but I'm only just hearing about it. Artic Base for homebrew 3ds lets your physical 3ds connect wirelessly to a modified version of the Citra 3ds emulator (available for android, linux, mac, and windows), so that the emulator can read game files from the 3ds and write save files back to it. You are emulating the game - contrary to some youtube videos you are NOT streaming the game from the 3ds - but all the files are taken from and go back to the 3ds, so there's no piracy involved and no need to find or download roms. Unless the games on your 3ds are themselves pirated, in which case shame on you you naughty child!
This allows a switch-like experience where you can play a game portably on your 3ds, then when you get home boot up the same game and the same save file to play on a bigger screen in higher resolution with a more comfortable controller via citra, saving your game back to the 3ds. It also lets you take advantage of Citra's ability to play multiplayer online even though the 3ds servers are down by emulating a local connection over the internet. It's also an easy option to stream or record gameplay if you're into that without the trouble of installing a capture card mod onto your 3ds.
Now, granted, this was all already possible by copying save files back and forth from your 3ds memory card to your computer, but to do that you still had to go through the bother of setting up citra and getting your game files on there - either by finding roms or by dumping the files yourself. That could be a pretty significant hassle, but Artic base handles it all for you.
There is a downside - every time you load or save anything in your game, that data has to be transfered between your 3ds and Citra over wifi, which does add a delay and some slowdown whenever that's happening. But most of the time gameplay runs very smoothly.
Anyway, Artic Base requires a modded 3ds. Instructions can be found HERE. The process isn't very difficult, but read the directions carefully and take your time, as there's always a risk of breaking a device when installing custom firmware if you mess something up. Don't rely on video guides for this process! if the video is out of date, it might give you instructions that are no longer correct for the current methods and files!
Even if you're not interested in Citra, modding adds so much utility to the 3ds that you really should look into it if you have one. Button remapping, using larger memory cards (I wouldn't go over 128gigs), backing up save files, backing up entire games so you don't lose access to them if the aging cartridges go bad, even community ports of entire games like Doom or Off or Fallout, access to the pretendo network which is slowly rebuilding online functionality for 3ds and wii, the ability to stream from your computer to your 3ds, access to h-shop to download game updates and patches no longer available from nintendo after the e-shop's closure, and so much more.
Anyway, once you have a modded 3ds, Artic Base can be found on the Universal Updater app. I prefer the .cia version over the .3dsx version, so you don't have to go through Homebrew Launcher every time you want to use it. If you want to install it manually instead, it can be found HERE.
You also need a modified version of Citra to connect to your 3ds, which can be found HERE.
30 notes
·
View notes
Text
UBUNTU TOUCH | DAY ONE
If you didn't see one of my previous posts, I've got a phone to experiment with, and I'm gonna be trying out various mobile operating systems! (Primarily linux based! Not that android isn't linux but lets be real.) please ignore my greasy ugly hand Installation Process: The installation actually wasn't that bad! Was kinda awkward trying to get the phone updated to the correct version without upgrading too far, but after that was dealt with everything else was taken care of very smoothly and easily with the UB Ports custom installer! Didn't have a fail state, nor did the phone brick! I'd rate this an 8/10! Setup and Tutorial: Setting up the phone after the install was very fast, frankly there wasn't much to set up. Thankfully it's not like Google or Apple where they ask for your firstborn son before even asking for your SIM card. Just needed to set up a password/passcode, set up my SIM (Which was thankfully automatic kinda, details later) and confirm a Wi-Fi connection if I wanted to!) Tutorial however, was a bit lackluster. While it was descriptive, it also only popped up on my first time seeing each screen. (E.g. I didn't get the tutorial for the phone app until I opened the phone app.) While I don't think this is necessarily a bad thing, it also means I would need to walk through every inbuilt app to make sure the tutorials are all done. kinda annoying in my personal opinion. Overall I'd rate this 6~7/10. Usage and Experience: For day one this isn't super important, however first impressions do matter for most people. The OS as a whole was very snappy, and never froze or lagged in any of my testing. Additionally, the pull-down shade is very nice! Could be simplified a little more so that you don't need to scroll sideways, and it would also be nice to see more settings overall since the system seems to be quite bare for settings at the moment. However one of the things that really bothers me as a button-enjoyer is the OS not having a button navigation method. The only way to navigate between screens is to swipe from the sides, top or bottom as gestures, similar to Apple and the recent Android iterations. These gestures don't even work perfectly either, which makes it more annoying that I don't have a home button or back button. If there is a home-swipe or back-swipe, then the tutorial did not detail it, and I cannot find it anywhere in the settings. Overall, it's a 4/10 but with LOTS of potential! Functionality: This focus' almost entirely on how it functions as a phone, and if it's problematic for any reason. So far it seems great outside of one issue, as commented on earlier (This is the details later bit lmao). Plugged an active SIM card into the phone and it automatically logged the APN and other important information which was very nice. Tested the mobile data and texting, and found no issues except for maybe being unable to send MMS (Need to double check that it was not a file size issue.) However, this entire time I've not had the ability to make or take calls. I'm not sure why, the APN, provider, and everything in the settings is correct to what I can tell. I may attempt to either reinstall the dialer application, or erase and manually set the APN in the event that might fix it. If I cannot get calling to work this score will look a lot uglier. Overall, it's a 7~8/10! for now.
App Availability: Seems great! The built in app-store, or "OpenStore" is pretty cool, and seems to have a lot of useful apps. I did notice a small fraction of android apps that I could use (Like Slack, thanks workplace -ﻌ-) but they were just WebUI apps, which isn't bad, but it's bad. I haven't attempted to set up or use Waydroid, but I will not have that change the score at all since using Android apps (kinda barely) defeats the purpose of an alternative operating system. Overall score, 8/10, but needs a deeper dive.
I'll likely put out another update at either 15 days or 30 days!
Whenever you guys think you want one!
8 notes
·
View notes
Text
Revisiting Wrap030 Disk Access
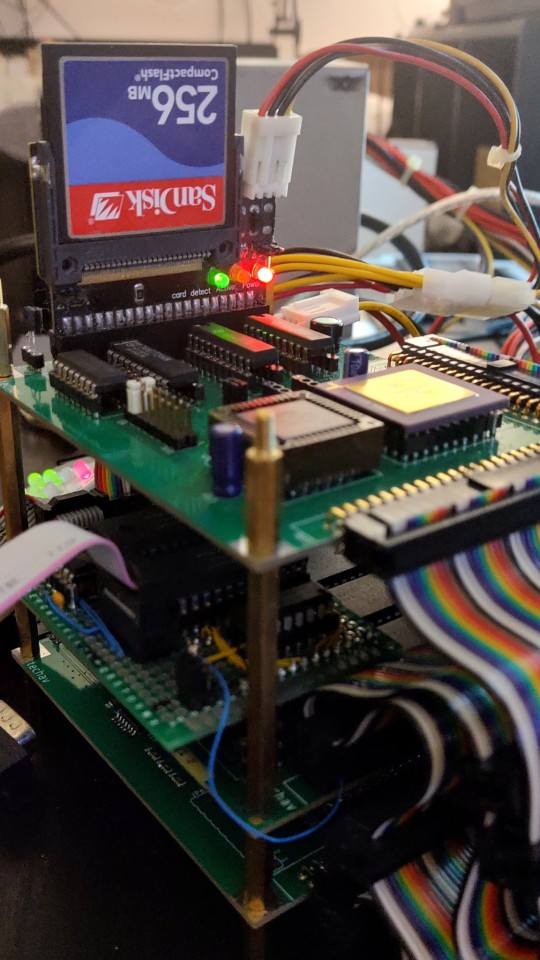
I have more ideas for projects than time or budget to work on them. Already this year I've gone completely through the design process for two new large homebrew projects that are currently too large for my project budget, plus a few small ones I never got around to ordering. So rather than spend more than I should taking on a new project, I decided to revisit an existing one.
It's been over a year since I last worked on the original Wrap030 project — my old stack-of-boards MC68030 system. Its current configuration includes the main board with CPU, ROM, RAM, UART, & glue logic; a hand-wired breakout board to add a second UART; a custom video output board; and a mezzanine board with FPU and provision for an IDE disk that is not yet working. It has been functional in this configuration since last February.
My goal for this project from the beginning was to build something capable of running a proper operating system, like Unix System V or Linux. To do that though, I'm going to need to get disk access working.
I had started on disk access, but didn't quite have it functional when I turned my focus to integrating all of boards into the single Wrap030-ATX motherboard. I had added IDE cycles to the CPLD on the mezzanine board, and had added a few rough drafts of disk functions to my ROM. I set the project aside when I realized my function for checking dish presence was reporting a disk was present when there wasn't one.
I have worked with IDE before — my original 68000 project had an IDE port on it. I had gotten that project to the point where I could read a sector of data from the disk, but never could wrap my head around how to actually navigate even a simple file system like FAT16. It was this code that I had adapted for Wrap030, so when it didn't work, I assumed it was a problem with my logic.
Turns out I had just inadvertently clobbered a register in the disk check function. The logic worked just fine. I was able to write a couple quick BASIC programs to read a sector of data and even run code from the boot sector.
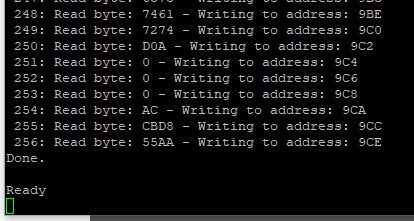

My assembly function for reading data from disk however was still not working.
I tried rewriting it.
I tried rewriting it in C instead of assembly.
I tried again, and again, and again. I added delays and loops and print statements and everything I could think of. I scoured datasheets, read though all the different release versions of the ATA specification, ported code from other projects, looked at every example of reading from an IDE disk I could find.
No matter what I did, I always got the same result.
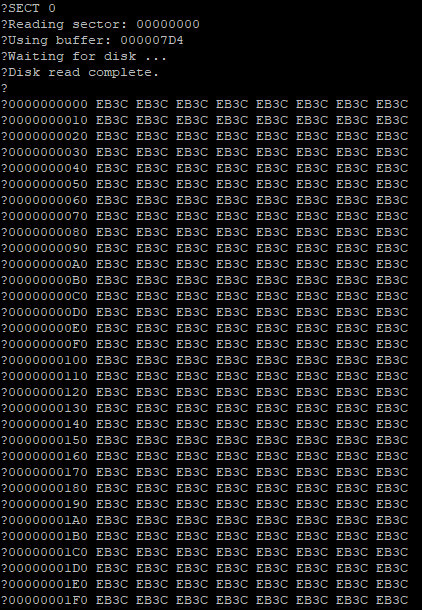
This did not make any sense. Reading from an IDE disk involves setting up the sector address, the number of sectors to transfer, sending a read command, and then reading the IDE data port 256 times per sector. Each time the data port is read, the disk will give another 16-bit word of data. But for some reason, all I was getting was the first word of data returned 256 times.
There is nothing in the specification to explain this.
I knew there was nothing wrong with my logic, because I could read the data just fine with my BASIC program or by manually poking the right addresses using the monitor. Maybe there was some edge case affecting timing when running in assembly, but even adding delay loops and print statements didn't have any effect.
I reached out for help. I got great feedback on my read functions and my timing and how IDE and CompactFlash cards worked, but still could not solve this problem.
But then @ZephyrZ80 noticed something —
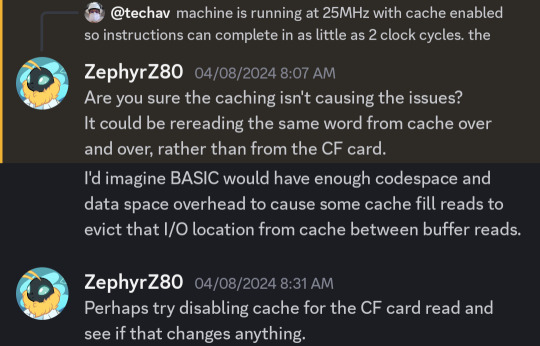
I had shared my code and was explaining that I had added some extra NOP instructions to enforce minimum time between IDE access cycles in PIO-0 mode. At 25MHz with cache enabled, the 68030 can complete an instruction in as little as 80ns, so a few NOPs would ensure enough time elapsed between cycles.
With cache enabled.
… cache enabled.
… cache.
The 68030 has 256 bytes of data cache. My disk read function is running in a tight loop that only really hits a few addresses; not nearly enough to invalidate and flush the entire 256 bytes of cache. The CPU does have a cache inhibit signal to use with peripherals that return new data on subsequent access to the same address, but it turns out I was only asserting it when accessing the UART on the main board.
It's a simple enough hypothesis to test. When I initially added support in my ROM for enabling cache at startup, I included user functions for enabling and disabling cache.
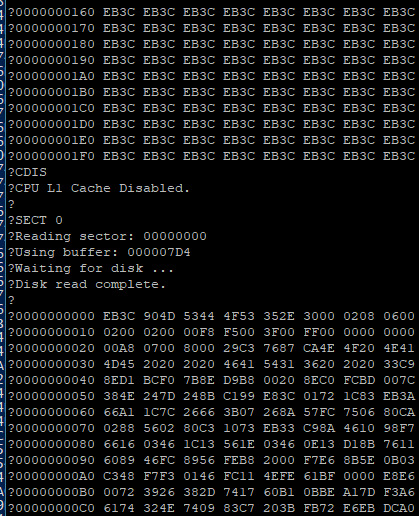
… It was cache all along.
Now I need to add some way to inhibit cache while accessing the IDE port, and then I can move on to trying to use the disk for loading programs.
41 notes
·
View notes
Text
How to find hidden processes and ports on Linux/Unix/Windows
16 notes
·
View notes
Text
I started writing all of this in the tags, but then I got so many of them it just hit me it should be a whole post, so, here: i used linux (arch-based specifically) as my daily driver OS for 2 years and i loved it and it's great but it's not the solution
in fact the leap from ''i don't know how to move files between folders'' to linux is going to be too advanced for most people and make them more likely to give up. especially if a program they use and like doesn't have a native linux package.
like in my own experience i couldn't find a music player that could rival foobar for me on features so i just kept using foobar. and that meant that one of the first things i installed on a fresh linux install was wine. and some distros deal don't give you an easy way to do that. some do not even give you easy ways to install anything at all. and nobody who is not already comfortable with doing "advanced" user things on their preferred system is going to be suddenly more confident about using the linux terminal package installation process.
sometimes features that you don't even have to worry about on windows/native OS don't get automatically carried on linux distro installations. for example, my laptop's wifi card's drivers! it's not an old or obscure laptop - it's a lenovo legion. you know, a fairly popular laptop model! i had to urgently look for my ethernet cable and spent 3 days googling in my free time to figure out what driver i needed to install for my specific card and then way too much time fighting pamac over it because there were 3 different packages that had the name of my card but only one of them worked. or the fact that i searched for 2 years and still couldn't find a way to lower my screen's refresh rate, which was stuck at the max 165hz. so, you know, don't take your laptop off charging because you can't put it in a lower battery refresh rate, and just deal with the judder on movies because that's not going away. i lived with all of those issues and the inconvenience because to me, they weren't ~that~ big of a deal and at least some of them i could bypass or fix with a little bit of time. most people are not going to be fine with the inconvenience, especially if they remember using an OS where those same issues never even came up.
one thing i DO recommend people to do with linux is to keep a usb stick with a flashed linux distro that has a live mode, because you can use it without installing the OS. so if your main OS gets corrupted because of an update or anything else happens to it, you can just plug your linux usb into the usb port and boot into the live usb and have access to your files and go online if you want. on some distros you can even install programs on top of the base live distro, they are probably going to be gone next time you log in though. you'll need to learn how to access your bios menu, but it's significantly more user-friendly now than it was even a decade ago. if you, like me, have a fear of accidentally messing up your windows/etc OS and corrupting files in such a way that your computer just bricks itself basically, having that back-up linux live usb can do a lot for that anxiety. it definitely does mine!
bottom line don't offer people with no computer literacy linux as a user-friendly alternative. they WILL get confused by it and never want to try again in the future. offer them ways to learn their preferred system instead. in fact, chromeOS which powers chromebooks is a linux system. linux is not a catch all solution to computer literacy and never was
We need to lay more blame for "Kids don't know how computers work" at the feet of the people responsible: Google.
Google set out about a decade ago to push their (relatively unpopular) chromebooks by supplying them below-cost to schools for students, explicitly marketing them as being easy to restrict to certain activities, and in the offing, kids have now grown up in walled gardens, on glorified tablets that are designed to monetize and restrict every movement to maximize profit for one of the biggest companies in the world.
Tech literacy didn't mysteriously vanish, it was fucking murdered for profit.
#and also as an addon i don't consider myself a proficient user in linux systems or even windows that i have more familiarity with#but i know that i have enough computer literacy to know what to google and not get scared off by words like ''kernel'' and ''sudo''#this is actually my experience using linux as a somewhat pc literate user who doesn't know a lot about the system#or as you can also put it. an average desktop user. exactly like someone who you're inviting to try linux (maybe a bit more prepared)#and my experience was probably on the happier side because i really liked using it as my main OS. i still have a dual boot set up#i just don't log in to my linux system very often anymore. for most people in a similar starting position it would probably not go the same#silicon valley horror#electric sheep#ń txt
78K notes
·
View notes
Text
Linux netstat Command Explained | Monitor & Troubleshoot Network Connections
Master the netstat command in Linux and learn how to monitor network connections, check open ports, and troubleshoot connectivity issues like a pro! Whether you’re a system administrator or a developer, this tutorial will help you analyze network traffic and improve security.
🔹 In This Video, You’ll Learn: ✔️ What is netstat, and why is it useful? ✔️ How to check active network connections 🔍 ✔️ How to list listening ports on Linux servers 🖥️ ✔️ How to find which process is using a port 🚀 ✔️ How to analyze network statistics and troubleshoot issues
💡 Commands Used in This Video: netstat -tun netstat -tuln netstat -tulpn netstat -s netstat -rn
youtube
1 note
·
View note
Text
Gelluloid Domination: Build Your Gel-Powered Army

Gelluloid Domination the fast-paced strategic and tactical game is coming to Linux with Windows PC. Thanks to Tractor Set GO for their brilliant creativity that makes this project shine. Which you can find on Steam already. get ready to dive into an epic cell-battling adventure with Gelluloid Domination – the latest fast-paced strategy now live on Steam! Developed by the creative minds at Tractor, Set, Go! from Cluj-Napoca, Romania, this title is due to test your strategic skills and also keep you on the edge of your seat with fast-paced tactical moves. In Gelluloid Domination, you kick off your journey with a single, fragile cell. But don’t be misled by its small size — this little cell is your ticket to building a massive, gel-powered army. Your mission? Grow, adapt, and conquer every inch of the network. Every move you make matters. Will you expand your territory, or will your rivals steal your thunder? The choice is yours, and every decision writes the story of your domination. And a native build is on the way.
Porting to native Linux is definitely in our short-term roadmap (we expect 4-6 weeks from now).
Tractor Set GO's nearly there – Gelluloid Domination is 98% ready for Linux. They just need to tweak a few shaders and do some extra testing. Since they're using Unity 3D, porting it has been a smooth process. The game mechanics are refreshingly simple. All you need to do is transfer gel to capture nearby cells and manage your gel production. However, don’t let that fool you into thinking it’s an easy ride. Timing is everything in Gelluloid Domination. You must constantly watch your opponents, plan your moves, and be ready to switch strategies at a moment’s notice. It’s simple on the surface but packs a punch with layers of challenge and excitement.
Gelluloid Domination Official Launch Trailer
youtube
One of the best things about the gameplay is that it offers over 80 hand-crafted missions. Since every mission has been designed with care to throw a unique challenge your way. Whether you’re dominating in classic mode, tackling survival challenges, racing against the clock, or filling up reservoirs, there’s a fresh and fun twist every time you play. No two battles are ever the same! This title also features a deep tech tree that lets you upgrade your arsenal. Unlock offensive mutations like Medusa, Spike, and even explosive surprises, along with defensive upgrades such as turrets. With dozens of enhancements available, you can tailor your play style to suit both casual gaming and hardcore strategy sessions. Feeling competitive? The Gelluloid Domination smart AI opponents are ready to fight hard just like you. You can crank up the difficulty for a heart-pounding challenge or dial it down if you’re in the mood for a more relaxed play session. And for those of you who like to tinker with every little detail, there are advanced features like Continuous Send, Chain Linking, and a toggle between Passive and Aggressive modes. Plus, handy cell information panels give you a clear look at the numbers behind your moves. At its core, Gelluloid Domination is all about making bold moves and watching your empire grow. It’s also a fast-paced strategic and tactical game that mixes straightforward controls with a dash of drama, and endless replayability. So grab your controller, call in your friends, and get ready to dominate the network. Your cell empire awaits on Steam. But coming to Linux with Windows PC.
#gelluloid domination#strategy#tactical#linux#gaming news#tractor set go#ubuntu#windows#pc#unity#Youtube
1 note
·
View note
Text
How to Choose the Right Laptop on Rent in Airoli for Your Needs.

A laptop has become an essential tool for professionals, students, and business owners alike.
However, buying a new laptop isn’t always feasible, especially for short-term needs or when working on a tight budget.
That’s where renting a laptop comes in as a smart and practical choice.
If you're in Airoli, a bustling hub of activity and growth, finding the right laptop on rent in Airoli can be a game-changer.
But how do you choose the right one? Here's a step-by-step guide to help you make an informed decision.
1. Understand Your Needs
Before you start looking for a laptop on rent in Airoli, clearly define your requirements.
For Work: If you need a laptop for work, consider its processing power, memory, and battery life.
For heavy software like graphic design tools or video editing, opt for high-performance laptops.
For Studies: Students may need basic laptops for research, online classes, and assignments. Prioritize lightweight models with good battery life.
For Gaming or Entertainment: Gamers or entertainment enthusiasts should look for laptops with dedicated GPUs, high-resolution screens, and excellent sound quality. Knowing your primary use will narrow down the choices.
2. Set a Budget
Renting a laptop is cost-effective, but prices can vary based on the model, specifications, and rental duration.
Decide how much you're willing to spend per month and stick to your budget. Compare different rental providers in Airoli to ensure you're getting the best deal.
3. Research Local Providers
Airoli is home to several reliable laptop rental services. Look for providers with positive reviews and a good track record.
Search online or ask for recommendations from locals to find trusted rental companies. Some providers might even offer doorstep delivery, saving you time and effort.
4. Check Laptop Specifications
When renting, ensure the laptop's specifications align with your needs:
Processor: Choose an Intel i5/i7 or AMD Ryzen processor for multitasking or heavy applications. Basic tasks can be handled by an i3 processor.
RAM: 4GB is suitable for basic use, while 8GB or more is ideal for work or gaming.
Storage: Decide between SSD (faster) or HDD (larger capacity).
Operating System: Ensure the laptop comes with the required OS, like Windows, visionIT Rent macOS, or Linux. These details play a crucial role in ensuring a smooth and efficient experience.
5. Inspect the Laptop Condition
Always inspect the laptop before finalizing your rental agreement.
Check for physical damage like scratches or dents.
Ensure the keyboard, trackpad, and ports are functioning properly.
Test the screen for any dead pixels or discoloration.
Confirm that the battery holds a charge well. A thorough inspection can save you from future headaches.
6. Understand the Rental Agreement
Carefully read the rental terms and conditions:
Duration: Does the provider offer flexible rental periods?
Pricing: Are there any hidden charges?
Maintenance: Who handles repairs or replacements if the laptop malfunctions?
Security Deposits: Some providers might require a refundable deposit. Ensure you’re clear about the refund process. A transparent agreement protects both you and the rental provider.
7. Inquire About Additional Services
Some laptop rental companies in Airoli offer additional benefits:
Technical Support: Assistance for software installation or troubleshooting.
Upgrades: The ability to switch to a better model during the rental period.
Accessories: Options to rent peripherals like a mouse, external keyboard, or monitor. These extras can enhance your rental experience.
8. Evaluate Customer Support
Good customer support is essential. Choose a provider that is responsive and willing to assist with any issues during the rental period. Check reviews or speak to previous customers to gauge the quality of their service.
9. Plan for Long-Term Use
If you’re considering renting for an extended period, discuss discounts or customized plans with the provider. Long-term rentals often come with better pricing and benefits.
10. Eco-Friendly Option
Renting a laptop is also an environmentally friendly choice. By opting for a laptop on rent in Airoli, you contribute to reducing electronic waste and promoting sustainable practices.
Conclusion
Renting a laptop in Airoli is a convenient and affordable solution for a variety of needs.
By understanding your requirements, comparing options, and choosing a reliable provider, you can make the most of this service.
Whether you need a high-performance laptop for work or a simple one for basic use, following these steps will ensure you get the right device without any hassle.
So, the next time you’re in need of a laptop on rent in Airoli, use this guide to simplify your decision-making process.
Renting isn’t just cost-effective; it’s also a smart way to stay updated with the latest technology without a long-term commitment.
0 notes
Text
Use Intel Gaudi-3 Accelerators To Increase Your AI Skills

Boost Your Knowledge of AI with Intel Gaudi-3 Accelerators
Large language models (LLMs) and generative artificial intelligence (AI) are two areas in which Intel Gaudi Al accelerators are intended to improve the effectiveness and performance of deep learning workloads. Gaudi processors provide efficient solutions for demanding AI applications including large-scale model training and inference, making them a more affordable option than typical NVIDIA GPUs. Because Intel’s Gaudi architecture is specifically designed to accommodate the increasing computing demands of generative AI applications, businesses looking to implement scalable AI solutions will find it to be a highly competitive option. The main technological characteristics, software integration, and upcoming developments of the Gaudi AI accelerators are all covered in this webinar.
Intel Gaudi Al Accelerators Overview
The very resource-intensive generative AI applications, as LLM training and inference, are the focus of the Gaudi AI accelerator. While Intel Gaudi-3, which is anticipated to be released between 2024 and 2025, promises even more breakthroughs, Gaudi 2, the second-generation CPU, enables a variety of deep learning enhancements.
- Advertisement -
Intel Gaudi 2
The main attributes of Gaudi 2 consist of:
Matrix Multiplication Engine: Hardware specifically designed to process tensors efficiently.
For AI tasks, 24 Tensor Processor Cores offer high throughput.
Larger model and batch sizes are made possible for better performance by the 96 GB of on-board HBM2e memory.
24 on-chip 100 GbE ports offer low latency and high bandwidth communication, making it possible to scale applications over many accelerators.
7nm Process Technology: For deep learning tasks, the 7nm architecture guarantees excellent performance and power efficiency.
These characteristics, particularly the combination of integrated networking and high memory bandwidth, make Gaudi 2 an excellent choice for scalable AI activities like multi-node training of big models. With its specialized on-chip networking, Gaudi’s innovative design does away with the requirement for external network controllers, greatly cutting latency in comparison to competing systems.
Intel Gaudi Pytorch
Software Environment and Stack
With its extensive software package, Intel’s Gaudi platform is designed to interact easily with well-known AI frameworks like PyTorch. There are various essential components that make up this software stack:
Graph Compiler and Runtime: Generates executable graphs that are tailored for the Gaudi hardware using deep learning models.
Kernel Libraries: Reduce the requirement for manual optimizations by using pre-optimized libraries for deep learning operations.
PyTorch Bridge: Requires less code modification to run PyTorch models on Gaudi accelerators.
Complete Docker Support: By using pre-configured Docker images, users may quickly deploy models, which simplifies the environment setup process.
With a GPU migration toolset, Intel also offers comprehensive support for models coming from other platforms, like NVIDIA GPUs. With the use of this tool, model code can be automatically adjusted to work with Gaudi hardware, enabling developers to make the switch without having to completely rebuild their current infrastructure.
Open Platforms for Enterprise AI
Use Cases of Generative AI and Open Platforms for Enterprise AI
The Open Platform for Enterprise AI (OPEA) introduction is one of the webinar’s main highlights. “Enable businesses to develop and implement GenAI solutions powered by an open ecosystem that delivers on security, safety, scalability, cost efficiency, and agility” is the stated mission of OPEA. It is completely open source with open governance, and it was introduced in May 2024 under the Linux Foundation AI and Data umbrella.
It has attracted more than 40 industry partners and has members from system integrators, hardware manufacturers, software developers, and end users on its technical steering committee. With OPEA, businesses can create and implement scalable AI solutions in a variety of fields, ranging from chatbots and question-answering systems to more intricate multimodal models. The platform makes use of Gaudi’s hardware improvements to cut costs while improving performance. Among the important use cases are:
Visual Q&A: This is a model that uses the potent LLaVA model for vision-based reasoning to comprehend and respond to questions based on image input.
Large Language and Vision Assistant, or LLaVA, is a multimodal AI model that combines language and vision to carry out tasks including visual comprehension and reasoning. In essence, it aims to combine the advantages of vision models with LLMs to provide answers to queries pertaining to visual content, such as photographs.
Large language models, such as GPT or others, are the foundation of LLaVA, which expands their functionality by incorporating visual inputs. Typically, it blends the natural language generation and interpretation powers of big language models with image processing techniques (such those from CNNs or Vision Transformers). Compared to solely vision-based models, LLaVA is able to reason about images in addition to describing them thanks to this integration.
Retrieval-Augmented Generation (RAG) or ChatQnA is a cutting-edge architecture that combines a vector database and big language models to improve chatbot capabilities. By ensuring the model obtains and analyzes domain-specific data from the knowledge base and maintains correct and up-to-date responses, this strategy lessens hallucinations.
Microservices can be customized because to OPEA’s modular architecture, which lets users change out databases and models as needed. This adaptability is essential, particularly in quickly changing AI ecosystems where new models and tools are always being developed.
Intel Gaudi Roadmap
According to Intel’s Gaudi roadmap, Gaudi 2 and Intel Gaudi-3 offer notable performance gains. Among the significant developments are:
Doubling AI Compute: In order to handle the increasing complexity of models like LLMs, Intel Gaudi-3 will offer floating-point performance that is 2 times faster for FP8 and 4 times faster for BF16.
Enhanced Memory Bandwidth: Intel Gaudi-3 is equipped with 1.5 times the memory bandwidth of its predecessor, so that speed won’t be compromised when handling larger models.
Increased Network capacity: Intel Gaudi-3’s two times greater networking capacity will help to further eliminate bottlenecks in multi-node training scenarios, which makes it perfect for distributing workloads over big clusters.
Additionally, Gaudi AI IP and Intel’s GPU technology will be combined into a single GPU form factor in Intel’s forthcoming Falcon Shores architecture, which is anticipated to launch in 2025. As part of Intel’s ongoing effort to offer an alternative to conventional GPU-heavy environments, this hybrid architecture is expected to provide an even more potent foundation for deep learning.
Tools for Deployment and Development
Through the Intel Tiber Developer Cloud, which offers cloud-based instances of Gaudi 2 hardware, developers can utilize Gaudi accelerators. Users can test and implement models at large scale using this platform without having to make investments in on-premises infrastructure.
Starting with Gaudi accelerators is as simple as following these steps:
Docker Setup: First, users use pre-built images to build up Docker environments.
Microservices Deployment: End-to-end AI solutions, such chatbots or visual Q&A systems, can be deployed by users using tools like Docker Compose and Kubernetes.
Intel’s inherent support for monitoring tools, such as Prometheus and Grafana, enables users to manage resource utilization and performance throughout their AI pipelines.
In summary
Enterprises seeking an efficient way to scale AI workloads will find a compelling solution in Intel’s Gaudi CPUs, in conjunction with the extensive OPEA framework and software stack. With Gaudi 2’s impressive performance and Intel Gaudi-3‘s upcoming improvements, Intel is establishing itself as a formidable rival in the AI hardware market by offering a reasonably priced substitute for conventional GPU-based architectures. With OPEA’s open and modular design and wide ecosystem support, developers can quickly create and implement AI solutions that are customized to meet their unique requirements.
Read more on govindhtech.com
#IntelGaudi3Accelerators#AISkills#AIapplications#IntelGaudi3#Gaudi2#KernelLibraries#chatbots#LargeLanguage#VisionAssistant#LLaVA#intel#RetrievalAugmentedGeneration#RAG#news#Tools#IntelTiberDeveloperCloud#Prometheus#EnterpriseAI#GenerativeAI#technology#technews#govindhtech
0 notes
Text
How to Optimize Your Computer Server for Maximum Performance?
Optimizing your computer server for maximum performance involves a series of steps that enhance its efficiency, reliability, and speed. Here are some detailed instructions to help you achieve this:
1. Hardware Optimization
a. Upgrade Server Hardware
RAM: Ensure your server has sufficient RAM. Upgrade to ECC (Error-Correcting Code) RAM for better reliability.
Storage: Use SSDs (Solid State Drives) instead of HDDs (Hard Disk Drives) for faster read/write speeds.
CPU: Upgrade to a more powerful CPU with higher clock speeds and more cores.
Network Interface Cards (NICs): High-speed NICs, such as 10GbE, are used to handle increased network traffic.
b. Maintain Hardware
Regular Cleaning: Dust and clean server components to prevent overheating.
Monitor Hardware Health: Use tools to monitor temperatures, voltages, and fan speeds.
2. Software Optimization
a. Optimize Operating System (OS)
Choose the Right OS: Select an OS tailored to your server's role (e.g., Linux distributions like Ubuntu Server or CentOS for web servers).
Update Regularly: Keep the OS and all software up to date with the latest patches and security updates.
Remove Unnecessary Services: Disable or uninstall services and applications that are not needed.
b. Optimize Applications
Database Optimization: Use indexing and query optimization techniques. Consider database clustering for load balancing.
Web Server Optimization: For Apache, use modules like mod_deflate for compression. For Nginx, adjust worker processes and caching settings.
Caching: Implement caching mechanisms such as Memcached or Redis to reduce database load.
3. Network Optimization
a. Configure Network Settings
Adjust TCP/IP Settings: Optimize parameters such as TCP window size and timeout settings.
DNS Configuration: Use reliable and fast DNS services.
b. Network Security
Firewall Configuration: Use firewalls to block unnecessary ports and protect against attacks.
Use VPNs: Secure remote access with VPNs to ensure encrypted connections.
4. Performance Monitoring and Tuning
a. Use Monitoring Tools
System Monitoring: Tools like Nagios, Zabbix, or Prometheus can provide insights into system performance and alert you to issues.
Log Analysis: Regularly analyze logs to detect and resolve errors and performance bottlenecks.
b. Regular Performance Tuning
Load Balancing: Distribute workloads across multiple servers to prevent any single server from being overwhelmed.
Scalability Planning: Plan for future growth by considering horizontal and vertical scaling options.
5. Security Enhancements
a. Regular Security Audits
Vulnerability Scanning: Use tools like Nessus to identify and address vulnerabilities.
Penetration Testing: Conduct regular penetration tests to find and fix security weaknesses.
b. Data Protection
Backups: Implement regular, automated backups and test restore procedures.
Encryption: Use encryption for sensitive data, both in transit and at rest.
6. Energy Efficiency
a. Power Management
Use Energy-Efficient Hardware: Choose energy-efficient hardware components.
Configure Power Settings: Adjust power settings to reduce consumption during low-usage periods.
b. Cooling Optimization
Efficient Cooling Systems: Use advanced cooling systems to maintain optimal temperatures.
Hot and Cold Aisle Containment: Implement hot and cold aisle containment in data centers to improve cooling efficiency.
Conclusion
By systematically addressing these areas, you can significantly enhance your server's performance, reliability, and security. Regular monitoring, updates, and proactive maintenance are key to maintaining optimal server performance over time. You can check more at Netseg.me.
0 notes
Text
Forlinx FET3568-C SoM: The Efficient and Intelligent Main Control Choice for Vending Machines
1. Product Description
Vending machines, combining modern technology with the idea of convenient shopping, have become essential in our lives. It breaks through the constraints of time and space, providing us with round-the-clock uninterrupted product purchasing services. Whether in busy transportation hubs or quiet residential areas, you can always find its presence.

2. Components:
Body Compartment: Made from high-strength, corrosion-resistant metal materials to ensure the stability and durability of the vending machine. The warehouse's interior is well-designed and can be adjusted according to the size of the goods to maximize the use of storage space.
Payment System: Integrated with multiple payment methods including coins, bills, card swiping, and mobile payments, satisfying various consumer payment needs.
Display and operation: HD touchscreen shows product information and purchase process, simplifying steps to enhance user experience.
Product Delivery System: Uses precise mechanics and sensors for accurate, fast delivery to the outlet after payment.
Communication Management System: Enables real-time monitoring, sales data analysis, and remote fault diagnosis and repair of vending machines via wireless network.
Business Logic Topology

The vending machine's main control system acts as its operational core, akin to its "brain", overseeing and coordinating each module's functions. With the ongoing development of IoT, big data, and AI, automation has become an inevitable trend in the vending machine industry. This has led to new demands for the main control systems, focusing on:
Core Controller: It is essential to choose a stable, reliable, and high-performance core controller to ensure the overall logic control and data processing capabilities of vending machines.
Device Stability: It requires 24/7 uninterrupted operation, necessitating high stability and durability in both hardware and software. Specifically, the software system should have fault self-check and automatic recovery capabilities.
Scalability and Compatibility: To meet various scenarios and demands, the main control system of vending machines needs to be scalable. As products evolve, the main control system should be compatible with new hardware and software standards.
Payment Security: As payment methods diversify, ensuring the security of the payment process has become increasingly important. Vending machines need to guard against various security threats, such as data breaches and fraudulent activities.
AI Integration: Vending machines need to have intelligent recognition capabilities and data analysis abilities to recommend products based on users' purchasing preferences.
FET3568-C system on module(SoM) from Forlinx Embedded Systems offers high performance, low power consumption, and rich functionality, making it ideal for vending machines for these reasons:
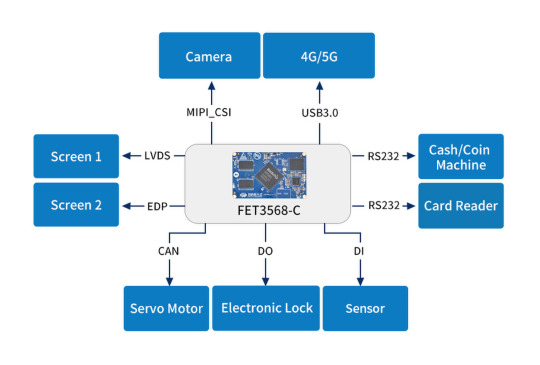
Powerful Performance: FET3568-C SoM is based on the Rockchip RK3568 processor, which features a quad-core 64-bit Cortex-A55 architecture with a clock speed of up to 2.0GHz. It supports lightweight edge AI computing and delivers strong computational and processing capabilities. Such performance meets the high demands of logic control and data processing for vending machine control systems, ensuring efficient and stable operation of the vending machines.
Rich Interfaces and Expandability: The FET3568-C SoM offers 3 x PCIe slots, 4 x USB ports, 3 x SATA3.0 controllers, and 2 x Gigabit Ethernet ports. It supports 5 x display interfaces including HDMI2.0, eDP, LVDS, RGB Parallel, and MIPI-DSI, with up to three simultaneous display outputs. These interfaces provide great convenience for expanding the functionality of vending machines, enabling customized development to meet various scenarios and requirements.
Multi-OS Support: FET3568-C SoM supports multiple operating systems including Linux, Android 11, Ubuntu, and Debian 11. This flexibility allows developers to choose the most suitable operating system according to actual needs, thereby simplifying the software development process and improving development efficiency. Meanwhile, Forlinx Embedded has made numerous optimizations in software, such as introducing a 4G watchdog process. This design ensures that the 4G communication function can automatically recover after a disconnection, significantly improving the stability and reliability of the vending machine's network communication.
Advanced Security: In terms of security, the FET3568-C hardware can integrate encryption chips and trusted root modules. These hardware-level security measures provide solid protection for system information security. The ability to verify software integrity and authenticity from the hardware level effectively prevents the intrusion of malicious software and the risk of system tampering.
High Stability: FET3568-C has undergone rigorous environmental temperature testing, stress testing, and long-term stability operation testing, ensuring stable and reliable performance in various terminals and operational environments. This is crucial for vending machines that require 24/7 uninterrupted operation, as it can significantly reduce failure rates and enhance user experience.
In summary, the FET3568-C SoM not only features robust performance and stability, but also offers flexible operating system options, optimized software design, rich interfaces, and powerful expandability. These features make it an ideal choice for vending machine control solutions, capable of meeting the evolving needs of the industry.
Originally published at www.forlinx.net.
0 notes
Text
does vpn change local ip
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn change local ip
VPN Definition
A Virtual Private Network (VPN) is a technology that allows you to create a secure connection over the internet. It encrypts your internet traffic and directs it through a remote server, hiding your online activities from prying eyes.
Using a VPN provides you with anonymity and privacy online by masking your IP address and location. This is especially useful when accessing public Wi-Fi networks, as it protects your data from potential hackers or snoopers on the same network.
VPN services are commonly used by individuals who want to bypass geo-restrictions and access content that is not available in their location. By connecting to a server in a different country, users can access websites and services that may be blocked in their own region.
Businesses also utilize VPNs to allow employees to securely access company resources from remote locations. By creating a secure tunnel between the employee's device and the company's network, sensitive information is protected from interception.
In addition to security and privacy benefits, VPNs can also improve internet performance by reducing bandwidth throttling imposed by internet service providers. This can result in faster streaming speeds and smoother online gaming experiences.
Overall, a VPN is a versatile tool that offers security, privacy, and even performance benefits for individuals and businesses alike in today's digital age.
Local IP Address
A local IP address is a unique number assigned to a device connected to a local network. Unlike a public IP address, which is used to identify a device on the internet, a local IP address is specific to the internal network. This address allows devices within the same network to communicate with each other, share resources, and access the internet through a router.
Local IP addresses are typically assigned dynamically by a router using the Dynamic Host Configuration Protocol (DHCP). This means that each time a device connects to the network, it is given a temporary address from a pool of available addresses. However, devices can also be assigned static local IP addresses manually by network administrators to ensure consistency and easy access.
One of the most commonly used local IP address ranges is 192.168.x.x, where each 'x' can be any number from 0 to 255. This range allows for a large number of unique addresses to be assigned within a private network without causing conflicts with public IP addresses.
Understanding your device's local IP address can be useful for troubleshooting network issues, setting up port forwarding, accessing device settings, and more. To find your device's local IP address, you can check the network settings on your device or use command prompts like ipconfig (Windows) or ifconfig (Mac/Linux).
In conclusion, local IP addresses play a vital role in enabling communication within local networks and facilitating internet access for connected devices. Understanding how they work can help optimize network performance and ensure seamless connectivity.
VPN Functionality
A VPN, or Virtual Private Network, is a technology used to create a secure and encrypted connection over a less secure network, such as the internet. VPNs are commonly utilized to protect sensitive data, ensure online privacy, bypass geo-restrictions, and enhance online security.
The functionality of a VPN is based on the principle of tunneling, where data is encapsulated within a secure protocol and transmitted through a VPN server. This process safeguards the transmitted data from potential threats like hackers, government surveillance, or ISP monitoring. By encrypting the data, VPNs ensure that even if intercepted, it remains incomprehensible and secure.
Moreover, VPNs can change the user's apparent IP address, making it appear as if they are accessing the internet from a different location. This feature enables users to bypass geographical restrictions imposed by content providers or governments. For instance, individuals can access region-locked content, evade censorship, or access services restricted to specific locations.
In addition to security and privacy benefits, VPNs offer enhanced protection when connected to public Wi-Fi networks. These networks are prone to cyber attacks, but a VPN encrypts the data, making it virtually impossible for hackers to intercept sensitive information.
Overall, the main functionality of a VPN is to establish a secure and private connection, ensuring data privacy, online anonymity, and enhanced security for the users. Whether for personal use, business purposes, or accessing restricted content, VPNs play a crucial role in safeguarding internet activities and preserving online freedom.
IP Address Modification
Title: Understanding IP Address Modification: A Guide
In the digital landscape, an IP (Internet Protocol) address serves as a unique identifier for devices connected to a network. Whether it's your home network or the vast expanse of the internet, your device's IP address is akin to its virtual address. However, there are instances where modifying an IP address becomes necessary, either for security, privacy, or functionality reasons.
IP address modification involves altering the numerical label assigned to your device. This alteration can occur manually or automatically, depending on the specific requirements. Here's a breakdown of the reasons and methods for IP address modification:
Enhancing Privacy: Changing your IP address can help safeguard your online privacy. By frequently modifying your IP address, you can prevent websites and online services from tracking your browsing habits.
Avoiding Restrictions: In some cases, certain websites or online services may impose restrictions based on geographical locations. By modifying your IP address to appear as if you're accessing the internet from a different location, you can bypass such restrictions.
Network Troubleshooting: When encountering network connectivity issues, modifying your device's IP address can sometimes resolve the problem. This can involve releasing the current IP address and obtaining a new one from the network's DHCP (Dynamic Host Configuration Protocol) server.
Security Measures: Changing your IP address can be part of a broader security strategy, especially in thwarting potential cyber threats. By altering your IP address, you can make it more challenging for malicious actors to target your device directly.
Methods for IP address modification include manual configuration through network settings or using tools and software designed for this purpose. Additionally, some internet service providers (ISPs) may assign dynamic IP addresses that change periodically, offering a level of automatic modification.
In conclusion, IP address modification serves various purposes, from bolstering privacy to troubleshooting network issues. Understanding when and how to modify your IP address can enhance your online experience while ensuring the security and efficiency of your network connections.
Network Security
Network security is a crucial aspect of ensuring the privacy, integrity, and availability of data and resources in a networked environment. It involves the implementation of measures to protect the network infrastructure from various cyber threats and unauthorized access.
One of the fundamental components of network security is the implementation of firewalls, which act as barriers between a trusted internal network and untrusted external networks, such as the internet. Firewalls monitor and control incoming and outgoing network traffic based on predetermined security rules, thereby preventing unauthorized access and potential cyber attacks.
Encryption is another essential aspect of network security, which involves the process of converting data into a code to prevent unauthorized access during transmission or storage. By using encryption algorithms, sensitive information is scrambled into a format that can only be decrypted by authorized parties with the appropriate decryption key.
Regularly updating and patching network devices and software is also crucial for maintaining network security. Software vendors often release patches and updates to address security vulnerabilities and improve the overall security posture of network infrastructure. Failure to update software can leave networks susceptible to exploitation by cybercriminals.
Network security also involves implementing strong authentication mechanisms, such as multi-factor authentication, to verify the identity of users and devices accessing the network. By requiring multiple forms of verification, such as passwords, biometrics, or security tokens, organizations can enhance the security of their networks and prevent unauthorized access.
In conclusion, network security plays a vital role in safeguarding the confidentiality, integrity, and availability of data and resources within a networked environment. By implementing robust security measures, such as firewalls, encryption, software updates, and strong authentication, organizations can mitigate the risks posed by cyber threats and ensure the secure operation of their networks.
0 notes
Text
do you need to keepo mudfish open vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do you need to keepo mudfish open vpn
Mudfish VPN setup
Setting up Mudfish VPN is a straightforward process that allows users to enhance their online privacy and security. Mudfish VPN provides a secure and encrypted connection, ensuring that your online activities remain private and protected from prying eyes.
To set up Mudfish VPN, you first need to create an account on the Mudfish website and purchase credits to use their service. Once you have logged into your account, you can download the Mudfish VPN client for your operating system, whether it be Windows, macOS, or Linux.
After downloading the client, you can install it on your device and log in using the credentials from your Mudfish account. From there, you can select a server location to connect to and customize your settings according to your preferences.
Mudfish VPN offers a variety of features, including the ability to bypass geo-restrictions, access region-locked content, and protect your online identity. By routing your internet traffic through their secure servers, Mudfish VPN ensures that your data remains safe from hackers and surveillance.
Overall, setting up Mudfish VPN is a quick and easy way to enhance your online security and privacy. With its user-friendly interface and robust features, Mudfish VPN is an excellent choice for anyone looking to protect their online activities.
OpenVPN configuration
Title: A Comprehensive Guide to OpenVPN Configuration
OpenVPN stands out as one of the most reliable and versatile virtual private network (VPN) solutions available today. Its open-source nature, combined with robust security features and cross-platform compatibility, makes it a popular choice for businesses and individuals alike. However, configuring OpenVPN can seem daunting for beginners. Fear not, as this guide will walk you through the process step by step.
Install OpenVPN: Begin by installing OpenVPN on your server or virtual machine. You can find detailed installation instructions on the OpenVPN website, tailored to various operating systems.
Generate Certificates and Keys: OpenVPN relies on cryptographic certificates and keys for secure communication. Use the provided scripts or tools to generate these essential components. Ensure to keep them secure and accessible only to authorized users.
Configure Server: Edit the OpenVPN server configuration file to define parameters such as protocol, port, encryption algorithms, and network settings. Pay special attention to security-related options to safeguard your VPN against potential threats.
Set Up Client Configuration: Prepare client configuration files containing connection details and certificates/keys. Distribute these files to users who need access to the VPN, ensuring they understand proper usage and security practices.
Test Connectivity: Before deploying OpenVPN in a production environment, conduct thorough testing to verify connectivity and ensure all configurations are functioning as intended. Simulate various scenarios to anticipate and address potential issues.
Monitor and Maintain: Regularly monitor the performance and security of your OpenVPN deployment. Stay informed about software updates and security advisories to promptly address vulnerabilities and enhance overall reliability.
By following these steps and staying informed about best practices, you can configure OpenVPN effectively to meet your specific needs. Whether you're securing remote access for your organization or safeguarding your online privacy, OpenVPN provides a robust and customizable solution.
Network optimization tools
Network optimization tools are essential for businesses looking to maximize the performance of their networks and ensure seamless communication and data transfer. These tools help in improving network efficiency, reducing latency, and enhancing overall network security.
One of the key features of network optimization tools is bandwidth management. By prioritizing network traffic and ensuring that critical applications receive the necessary bandwidth, these tools help in enhancing network performance and preventing bottlenecks.
Another important aspect of network optimization tools is optimizing network configurations. By analyzing network settings and configurations, these tools can identify potential problems and inefficiencies, allowing network administrators to make necessary adjustments for optimal performance.
Additionally, network optimization tools often come equipped with monitoring and reporting capabilities. This allows network administrators to track network performance in real-time, identify issues as they arise, and take proactive measures to address them before they impact network operations.
Furthermore, network optimization tools can help in enhancing network security by identifying potential vulnerabilities and implementing necessary security measures to protect against cyber threats and unauthorized access.
Overall, network optimization tools play a crucial role in ensuring that business networks operate at peak performance levels. By utilizing these tools, businesses can improve network efficiency, enhance security, and provide a seamless communication experience for employees and customers alike.
VPN performance testing
Title: Maximizing Security and Speed: A Guide to VPN Performance Testing
Virtual Private Networks (VPNs) have become indispensable tools for ensuring online privacy and security. However, with the plethora of options available, it's crucial to select a VPN service that not only provides robust security features but also delivers optimal performance. VPN performance testing is essential to gauge the speed, reliability, and overall effectiveness of a VPN service.
When assessing VPN performance, several key factors come into play:
Speed: The primary concern for many users is how a VPN affects internet speed. Speed tests measure the latency, download, and upload speeds while connected to the VPN. It's important to conduct tests using various servers to determine the most suitable for your needs.
Server Locations: VPN servers' geographic locations can significantly impact performance. Testing should include connecting to servers in different regions to assess speed and latency variations.
Bandwidth Limitations: Some VPN providers impose bandwidth limitations, which can affect performance, especially for activities requiring high data transfer rates such as streaming or file sharing. Testing helps identify any restrictions and their impact on performance.
Protocol Selection: VPN protocols such as OpenVPN, L2TP/IPsec, and IKEv2/IPsec offer different levels of security and speed. Testing various protocols helps determine which strikes the best balance between security and performance.
Security Features: While performance is crucial, it should not come at the expense of security. VPN performance testing should evaluate encryption strength, DNS leak protection, and kill switch functionality to ensure comprehensive security measures are in place.
Compatibility and Ease of Use: Testing should also consider the compatibility of the VPN client with different devices and operating systems. A user-friendly interface and seamless connection process contribute to a positive user experience.
By conducting thorough VPN performance testing, users can make informed decisions and select a VPN service that meets their security and speed requirements. Whether prioritizing privacy or streaming capabilities, testing helps find the perfect balance between performance and protection in an increasingly connected world.
Internet traffic routing
Internet traffic routing is the process of directing data packets between different networks to reach their intended destinations efficiently. This crucial aspect of internet infrastructure ensures that information travels smoothly across the vast network of interconnected devices worldwide.
At its core, internet traffic routing involves making decisions about the best path for data packets to travel based on various factors such as network congestion, latency, reliability, and cost. These decisions are typically made by routing algorithms implemented in networking devices like routers and switches.
One of the fundamental protocols used for internet traffic routing is the Internet Protocol (IP). IP packets contain both the sender's and recipient's IP addresses, allowing routers to determine where to forward the packets based on destination addresses.
In addition to IP routing, Border Gateway Protocol (BGP) plays a crucial role in directing traffic between different autonomous systems (ASes) on the internet. BGP enables routers within ASes to exchange routing information and make informed decisions about the best paths to reach destinations outside their networks.
Internet traffic routing operates on a hierarchical structure, with multiple tiers of networks interconnected through peering and transit agreements. Tier 1 networks, also known as backbone networks, form the core of the internet and interconnect with each other to provide global reachability. Lower-tier networks, such as internet service providers (ISPs), connect to tier 1 networks to access the broader internet.
Efficient traffic routing is essential for optimizing network performance, minimizing latency, and ensuring reliable connectivity. As internet traffic continues to grow exponentially, advancements in routing technologies, such as software-defined networking (SDN) and traffic engineering, play a vital role in adapting to evolving demands and improving the overall internet experience for users worldwide.
0 notes
Text
do i need to change utorrent settings for vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i need to change utorrent settings for vpn
VPN setup for uTorrent
Setting up a VPN for uTorrent can enhance your online privacy and security while torrenting. uTorrent is a popular BitTorrent client that allows users to download and share files over the internet. However, torrenting without proper protection can expose your IP address to potential threats and monitoring by third parties. By using a VPN (Virtual Private Network) with uTorrent, you can encrypt your internet connection and mask your IP address, ensuring anonymity and preventing unauthorized access to your data.
Here's how to set up a VPN for uTorrent:
Choose a reliable VPN provider: Select a VPN service that offers fast speeds, strong encryption, and a no-logs policy to safeguard your online activities.
Subscribe to the VPN service: Sign up for a subscription plan that suits your needs and budget. Most VPN providers offer various subscription options, including monthly, yearly, and multi-year plans.
Download and install the VPN software: Once you've subscribed, download the VPN client software compatible with your device's operating system (Windows, macOS, Linux, etc.). Follow the installation instructions provided by the VPN provider.
Connect to a VPN server: Launch the VPN application and log in with your credentials. Choose a VPN server location from the list of available options. Connecting to a server in a location with favorable privacy laws is recommended.
Configure uTorrent to use the VPN: Open the uTorrent client and navigate to the settings menu. Look for the connection or proxy settings and enter the VPN server's IP address and port number provided by your VPN provider. Enable the option to use the proxy for peer-to-peer connections.
Test your VPN connection: Verify that your VPN is properly configured by visiting an IP checking website to confirm that your IP address is masked and your internet traffic is encrypted.
By following these steps, you can set up a VPN for uTorrent and enjoy a safer and more private torrenting experience. Remember to keep your VPN software updated and adhere to your VPN provider's terms of service to maximize security and anonymity.
Adjusting uTorrent settings with VPN
Adjusting uTorrent Settings with VPN
uTorrent, a popular BitTorrent client, offers efficient file-sharing capabilities, but it's essential to ensure your privacy and security while using it. Utilizing a Virtual Private Network (VPN) with uTorrent can enhance anonymity and protect against potential threats. Here's a guide on adjusting uTorrent settings to work seamlessly with a VPN:
Choose a Reliable VPN: Select a reputable VPN service known for its strong encryption and no-logs policy. Ensure compatibility with uTorrent and consider factors like speed and server locations.
Install the VPN Software: Download and install the VPN client on your device. Follow the setup instructions provided by the VPN provider to complete the installation process.
Connect to a VPN Server: Launch the VPN application and connect to a server location of your choice. Opt for a server with high speed and minimal latency to maintain smooth torrenting.
Configure uTorrent Settings: Open uTorrent and navigate to the preferences or settings menu. Look for the connection or network tab, where you'll find options to configure proxy settings.
Enable Proxy Support: Check the box for "Proxy Server" and enter the details provided by your VPN provider. This typically includes the server address, port number, and authentication credentials if required.
Test the Connection: Verify that uTorrent is successfully connected to the internet through the VPN by conducting a connection test or monitoring your IP address.
Adjust Bandwidth Settings: To optimize performance, adjust uTorrent's bandwidth settings to accommodate the VPN's encryption overhead. This may involve limiting upload/download speeds or adjusting the number of active torrents.
Ensure Kill Switch Protection: Some VPN clients offer a kill switch feature that automatically disconnects your internet connection if the VPN connection drops. Enable this feature to prevent accidental exposure of your IP address.
By following these steps, you can effectively adjust uTorrent settings to utilize a VPN, safeguarding your online privacy and security while enjoying seamless torrenting experiences. Remember to regularly update both uTorrent and your VPN software for the latest security enhancements.
VPN compatibility with uTorrent
A Virtual Private Network (VPN) is a crucial tool for enhancing your online privacy and security. However, when it comes to using a VPN with uTorrent, compatibility is a key consideration. uTorrent is one of the most popular BitTorrent clients for downloading files, and combining it with a VPN can provide an extra layer of protection.
When using a VPN with uTorrent, it encrypts your internet traffic, making it difficult for anyone to monitor your online activities, including your Internet Service Provider (ISP). This means that your uTorrent downloads remain private and secure from prying eyes.
Most quality VPN services are compatible with uTorrent, but it's essential to choose a VPN that supports P2P file sharing and offers fast download speeds. Some VPN providers even offer specific servers optimized for torrenting, ensuring a smooth and secure uTorrent experience.
It's worth noting that using a VPN with uTorrent may slightly impact your download speeds due to the encryption process. However, the trade-off for enhanced privacy and security is often considered worthwhile by many users.
In conclusion, VPN compatibility with uTorrent is a crucial factor to consider when striving for a secure and anonymous torrenting experience. By selecting a reliable VPN provider that supports P2P file sharing and offers fast speeds, you can enjoy peace of mind knowing that your online activities are protected while using uTorrent.
Optimal uTorrent configuration for VPN
When using uTorrent with a VPN, it is essential to optimize the settings for the best experience and protection. A VPN, or Virtual Private Network, encrypts your internet connection and masks your IP address, providing anonymity and security while torrenting. By configuring uTorrent and your VPN properly, you can ensure optimal performance and privacy.
Firstly, select a VPN provider that allows P2P file sharing and has fast connection speeds. Some popular VPNs for torrenting include NordVPN, ExpressVPN, and CyberGhost. Make sure to enable the VPN kill switch feature, which will automatically disconnect uTorrent if the VPN connection drops, preventing your real IP address from being exposed.
Next, configure uTorrent settings to work seamlessly with your VPN. Go to the uTorrent options menu and select Preferences. In the Connection section, input the port number provided by your VPN provider for optimal connectivity. Enable UPnP port mapping and randomize port each start to enhance security.
In the Bandwidth section, set the download and upload limits according to your internet speed to avoid throttling by your ISP. Enable protocol encryption to mask uTorrent traffic and make it harder to detect by network administrators.
Lastly, prioritize safety by enabling the IP binding feature in uTorrent, which allows you to bind it to the VPN interface, ensuring that uTorrent only works when connected to the VPN. Additionally, regularly check for software updates for both uTorrent and your VPN to patch any security vulnerabilities.
By following these steps to optimize your uTorrent configuration for VPN usage, you can torrent securely and privately while maintaining optimal performance.
Ensuring privacy with uTorrent and VPN
When using uTorrent to download or share files, ensuring your privacy is crucial to protect your online activities. One effective way to enhance your privacy and security while using uTorrent is by using a Virtual Private Network (VPN).
A VPN encrypts your internet connection, making it difficult for anyone to monitor your online activities, including your torrenting behavior. By hiding your IP address and routing your internet traffic through a secure server, a VPN adds a layer of anonymity that helps protect your privacy.
When choosing a VPN to use with uTorrent, look for one that offers strong encryption protocols, a no-logs policy, and a kill switch feature. Strong encryption ensures that your data remains secure, while a no-logs policy means that the VPN provider does not store any information about your online activities. The kill switch feature is essential as it automatically disconnects your internet connection if the VPN connection is lost, preventing your real IP address from being exposed.
Additionally, it is important to select a VPN provider that allows torrenting on their servers and offers fast connection speeds to avoid any interruptions during your file-sharing activities. Some popular VPN services that are known for their privacy features and compatibility with uTorrent include ExpressVPN, NordVPN, and CyberGhost.
By combining uTorrent with a reliable VPN service, you can enjoy a more private and secure torrenting experience while safeguarding your online privacy. Remember to always prioritize your privacy and security when engaging in any online activities, including file sharing with uTorrent.
0 notes
Text
DOCKER ORACLE APEX

Title: Powering Up Oracle APEX with Docker: A Streamlined Development and Deployment Workflow
Introduction
Oracle Application Express (APEX) is a powerful low-code development framework for building scalable, enterprise-grade web applications on Oracle databases. Docker simplifies application deployment by packaging everything—code, configurations, and dependencies—into portable and consistent containers. Combining these technologies results in a fantastic way to streamline your APEX development process.
Why Docker for Oracle APEX?
Portability: Build your APEX environment once, and then run it anywhere Docker is supported, from development machines to production servers.
Consistency: Eliminate “works on my machine” issues. Docker images provide the same environment everywhere.
Scalability: Scale your APEX application by easily replicating Docker containers as needed.
Isolation: Run different APEX versions or multiple applications on the same host without conflicts.
Enhanced DevOps: Integrate Docker into your CI/CD pipelines for automated builds, testing, and deployments.
Step-by-Step Guide
Prerequisites
Basic familiarity with Docker concepts
Obtain Oracle Database Image
The official Oracle Database container image is on the Docker registry: [invalid URL removed]
Pull the image: docker pull container-registry.oracle.com/database/express:latest
Get Oracle APEX
Download the latest Oracle APEX version from [invalid URL removed]
Create a Dockerfile
# Start with an Oracle Linux base image
FROM oraclelinux:8
# Install dependencies
RUN yum install -y unzip wget nano
# Install Oracle database prerequisites
# (Refer to Oracle documentation for the correct package list)
RUN yum install -y oracle-database-preinstall-21c
# Create directories for database and ORDS
RUN mkdir -p /u01/app/oracle/product/21c/dbhomeXE /u02/app/ords
# Set environment variables
ENV ORACLE_HOME=/u01/app/oracle/product/21c/dbhomeXE \
PATH=$ORACLE_HOME/bin:$PATH
# Copy Oracle database installation files (adjust for the version you downloaded)
COPY linuxx64_213000_db_home.zip /tmp
# Unzip the database installation
RUN cd /tmp && unzip linuxx64_213000_db_home.zip
# Run the database installation (follow Oracle’s guide)
RUN /tmp/database/install.sh # … provide necessary inputs
# Copy Oracle APEX and ORDS
COPY apex /tmp/apex
COPY ords /u02/app/ords
# Install APEX
WORKDIR /tmp/apex
RUN sqlplus / as sysdba @apexins SYSAUX SYSAUX TEMP /i/
# Install ORDS (refer to ORDS installation guides)
WORKDIR /u02/app/ords
RUN java -jar ords.war install advanced
# Expose ports
EXPOSE 1521 8080
# Start script for the container (adjust as needed)
COPY start.sh /
CMD [“/bin/bash”, “start.sh”
Run the Container
docker run -d -p 8080:8080 –name my-apex-container my-apex-image
Access Your APEX Application
Open a browser and access your APEX application at http://localhost:8080/ords/
Additional Notes
Persist database data using Docker volumes.
Explore more advanced Docker networking concepts.
Integrate with a reverse proxy like Nginx for better production setups.
youtube
You can find more information about Oracle Apex in this Oracle Apex Link
Conclusion:
Unogeeks is the No.1 IT Training Institute for Oracle Apex Training. Anyone Disagree? Please drop in a comment
You can check out our other latest blogs on Oracle Apex here – Oarcle Apex Blogs
You can check out our Best In Class Oracle Apex Details here – Oracle Apex Training
Follow & Connect with us:
———————————-
For Training inquiries:
Call/Whatsapp: +91 73960 33555
Mail us at: [email protected]
Our Website ➜ https://unogeeks.com
Follow us:
Instagram: https://www.instagram.com/unogeeks
Facebook: https://www.facebook.com/UnogeeksSoftwareTrainingInstitute
Twitter: https://twitter.com/unogeeks
0 notes
Text
Unveiling the Power of Embedded Mini PCs: Compact Marvels Redefining Computing
In today's fast-paced digital landscape, where space is a premium and performance is paramount, embedded mini PCs emerge as the unsung heroes of computing. These compact marvels pack a punch, offering a plethora of functionalities in a small form factor. From powering IoT devices to driving multimedia displays, embedded mini PCs are reshaping industries and revolutionizing how we perceive computing. For more info about industrial mini PC visit here.
Understanding Embedded Mini PCs
Embedded mini PCs, often referred to as single-board computers (SBCs), are complete computing systems integrated onto a single circuit board. Unlike traditional desktops or laptops, which come in large enclosures housing various components, embedded mini PCs condense processing power, memory, storage, and connectivity into a compact design.
The Versatility of Embedded Mini PCs
One of the defining characteristics of embedded mini PCs is their versatility. These tiny machines find applications across a wide range of industries:
IoT and Edge Computing:
Embedded mini PCs are the backbone of IoT (Internet of Things) devices. They have the power to gather, process, and send data from sensors and actuators instantly. Additionally, they excel in edge computing scenarios, where processing tasks are performed closer to the data source, reducing latency and enhancing efficiency.
Digital Signage and Kiosks:
In the realm of digital signage and interactive kiosks, embedded mini PCs are the top choice. Their compact size allows for discreet installation behind displays, while their robust performance ensures smooth content playback and seamless user interactions. From retail stores to transportation hubs, these mini PCs drive engaging digital experiences.
Industrial Automation:
Industries rely on embedded mini PCs for automation and control systems. Whether it's monitoring manufacturing processes, managing inventory, or controlling machinery, these rugged machines deliver reliability and stability in harsh environments. Their small footprint is particularly advantageous in space-constrained industrial settings.
Home Entertainment:
Embedded mini PCs have found their way into living rooms, powering home entertainment systems and media centers. With support for high-definition video playback and gaming, these miniature PCs offer a compelling alternative to traditional set-top boxes and gaming consoles. Their low power consumption and silent operation make them ideal companions for immersive multimedia experiences.
Key Features and Specifications
Embedded mini PCs come in a variety of configurations to suit diverse requirements. Some key features and specifications to consider include:
Processor: From energy-efficient ARM processors to high-performance x86 CPUs, embedded mini PCs offer a range of processing options to meet specific performance needs.
Memory: RAM capacity determines multitasking capabilities and overall system responsiveness. Mini PCs typically offer varying levels of RAM, with options for expansion in some models.
Storage: Whether it's eMMC flash storage for compactness or SATA/PCIe interfaces for high-speed SSDs, embedded mini PCs provide storage solutions tailored to different use cases.
Connectivity: Gigabit Ethernet, Wi-Fi, Bluetooth, and USB ports enable seamless integration with networks and peripherals, ensuring flexibility and connectivity.
Operating System Support: From Linux distributions to Windows and Android, embedded mini PCs support a wide range of operating systems, catering to diverse development and deployment preferences.
Conclusion: Empowering Innovation in a Compact Package
Embedded mini PCs embody the essence of innovation, offering a compelling blend of compactness, performance, and versatility. As technology continues to evolve, these miniature marvels will play an increasingly pivotal role in shaping the future of computing across industries. Whether it's driving IoT ecosystems, enhancing digital experiences, or powering industrial automation, embedded mini PCs stand as testaments to the boundless possibilities of compact computing. Embrace the power of miniaturization and unlock new horizons with embedded mini PCs!
0 notes